Ground leaps towards 100 years of dream
100% lightning protection,
100% guarantee
100% lightning protection,
100% guarantee
100% lightning protection,
100% guarantee




100% lightning protection, 100% guarantee, 10 years of persisting period
Up to 10 years of performance and quality assurance through PGS service agreement!
Electric shock prevention between electric train and
PSD & PSD equipment lightning/surge protection system
DC Decoupling Device is a device that protects insulation facilities of piping system lay underground from electrical corrosion (electric type)
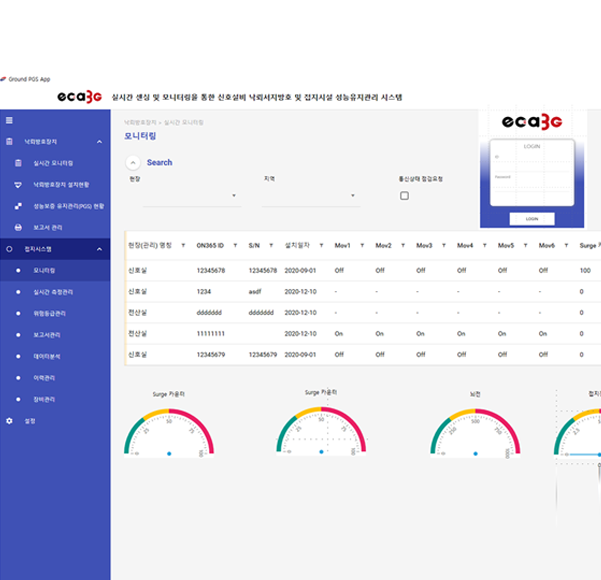
eca3G lightning protection integrated management monitoring system that monitors the performance/operation of integrated system, equipotentiality and TNC, and leakage current, and provides data analysis information
As a specialist in lightning protection and electric safety, Ground provides special PGS inspection service to protect customer’s equipment and inspect the system.
Lightning damage prevention measures
Electronic equipment is damaged, breaks down, or malfunctions whenever lightning strikes. Electronic equipment breaks down even if there is no lightening around. Earth leakage breaker trips and causes damages due to blackout whenever lightning strikes. CCTV, fire alarm controller, communication facility, and security system break down or malfunction whenever it rains. Electronic equipment breaks down or malfunctions frequently with no apparent reason. Lightning damage occurs despite the lightning rod, grounding, and SPD. There is significant recovery cost, loss of manpower, financial loss, and work damage due to lightning damage
What is the root cause of lightning damage?
Lightning rod pulls lightning, and grounding provides the entry for electricity. KSC-IEC was amended from independent ground to common ground in 2005, but it is still independent ground. Lightning reacts electrically at 300,000km/sec, and does a very wide damage. Lightning electricity breaks electronic equipment down through the land, water pipes, gas pipes, electric wire, or grounding cable. TN ground should be adopted in Korea, but can’t be adopted due to earth leakage breaker. standard common ground based on equipotential theory can’t be configured where there is ELB. It is because it’s difficult to determine or notify what the invisible lightning electricity did. The sites are not well aware because the amended KSC-IEC standard is promoted or trained.
What does it mean to dissipate the lightning damage?
It protects against damage, breakdown, or malfunction of electronic equipment despite lightning. Electronic equipment operates normally despite lightning around, and never breaks down. ELB never trips despite any lightning. CCTV, fire alarm controller, communication facility, and security system operate normally despite any lightning. There is absolutely no breakdown of electronic equipment caused by unknown reason. Electronic equipment can be operated stably without lightning rod and grounding. Lightning damages are completely prevented to protect against recovery cost, manpower, financial and business loss.
How can lightning damages be dissipated?
Solve the crashing issues between KS C-IEC’s TN method and extension regulations (ELB installation). Form common grounding based on equipotential theory and maintain the potential difference within 0.2V. In places with ELB, form TN method from the output through electromagnetic circuit separation. Improve the independent grounding of KS C-9609 in the past to the amended KS C-IEC standard in 2005. “Install lightning protection system (excluding lightning rod) and grounding facility” in Article 18 of the Radio Equipment Regulation. Review the error/problem thoroughly, and determine KS C-IEC standard correctly through perception change.
After we completely dissipate your lightning damages, decide to purchase after verification & Validation!
Maintain the TN method and equipotentiality below 0.1V through TNC model (performance-guaranteed product). In places with ELB, form TN method electromagnetic circuit separation of TNC model. Improve the independent grounding of KS C-9609 in the past to the amended KS C-IEC standard by installing eca3G. “Install lightning protection system (excluding lightning rod) and grounding facility” in Article 18 of the Radio Equipment Regulation by installing eca3G. In case of damage, offer 100% compensation through PL insurance.
What are the types of electric shock due to potential difference or electrocution?
전동차와 승강장안전문간의 전위차 발생으로 승강장안전문 제어계통 고장(오동작) 발생 전동차와 승강장 시설물(구조체, 승강장안전문 등) 접촉시 아크발생으로 위험요인 발생 전동차 승하차시 이용승객이 전동차와 구조물간 접촉시 전기감전 및 충격 발생 전동차 승하차시 카트가 승강장 연단과 전동차간 접촉시 전기충격에 의한 화재 발생 승강장 물유입시 전동차와 승강장간 전기충격 발생 승강장안전문 및 자동발판 절연파괴 등에 의한 전동차와 접촉시 전기감전 및 충격 발생
What is the root cause of serious damages due to potential difference?
전기철도차량이 선로를 통하여 운행시 레일전위는 필수적으로 발생한다. 2000년대 들어서면서 승강장에는 승강장안전문, 자동안전발판, 각종 통신장비등 많은 전자제어 장비들이 많이 시설되어 전기적인 위험요인 증대 특히 승강장안전문은 전기분야 전원 및 접지계통과 다른 환경으로 구축되어 등전위환경이 구축되어 있지 않아 전위차, 낙뢰, 서지에 취약한 현실. 각종 구조물(승강장안전문 등)에 절연처리를 하였으나 사용년수가 증가하고 절연물 파괴현상 증대로 감전 요인 증가.
What does it mean to dissipate the serious disasters due to potential difference?
한국전기설비규정(KEC)와 EN 표준규격에 다음과 같은 예방대책을 권고하고 있다. 1) 승강장안전문 및 구조물은 등전위본딩 시키고 표면은 견고하게 절연 2) 레일전위를 감소시키기 위해 접지보강 3) 전압제한소자 작용 등
What does it mean to dissipate the serious disasters due to potential difference?
레일전위, 누설전류, N-G간 전위, 허용 접촉전압 기준 범위 아래로 설비를 구성한다. 기준값 이상이면 레일등전위모듈과 서지감쇄모듈을 작동시키도록 설비를 구성한다. N-G간 등전위 모듈을 구성한다. 레일과 승강장안전문 등 승강장 구조물간 전위차 모니터링 설비를 구성한다.
After we completely dissipate your serious damages due to potential difference, decide to purchase after verification!
레일전위, 누설전류, N-G간 전위, 허용 접촉전압 기준을 1V 이내로 관리한다 승강장안전문의 낙뢰나 지락, 서지로부터 제어장치, 전원장치 등을 완벽히 방호한다 eca3G TNC PQR장치를 설치하여 전기철도에서 레일전위, 낙뢰 발생으로부터 안전상 문제점을 완벽히 해결한다. 만약 피해가 발생하면, PL 보험을 통하여 100% 책임배상을 제공한다
The Reality of the Lightning Rod, and lightning protection for electronic equipment, PSD accident prevention measures
Browse through No.1 Ground’s technical data,
studies, catalog, and PQR data.
1. Personal Information Collection and Collection Methods
2. Purpose of Collecting and Using Personal Information
3. Sharing and Providing Collected Personal Information
4. Delegation of Personal Information Processing
5. Retention and Usage Period of Collected Personal Information
6. Procedures and Methods for Destruction of Personal Information
7. Measures to Ensure the Security of Personal Information
8. Rights of Users and Legal Representatives and How to Exercise Them
9. Installation, Operation, and Rejection of Automatic Personal Information Collection Devices
10. Personal Information Manager and Department in Charge
11. Obligation to Notify
This policy is effective as of August 1, 2021.
1) Collected Items: The Company collects the following personal information for the purpose of managing inquiries related to the company, service/product inquiries, recruitment inquiries, website inquiries, reports of misconduct, and security reports.
- Required Information: Name, Company Name, Email, Contact Information
- The right to refuse consent and the disadvantages of refusal
- You have the right to refuse consent to the collection of required information.
- You have the right to refuse consent to the collection of optional information.
However, if you refuse consent, it may be impossible to respond to inquiries.
2) Collection Methods: The Company collects personal information through the following methods:
- 'Online Inquiry' Menu
The Company utilizes the collected personal information for the following purposes:
- Providing feedback and management for customer inquiries such as company-related inquiries, service/product inquiries, and website inquiries.
The Company, in principle, does not provide users' personal information to external parties. However, exceptions are made in the following cases:
- If users have given prior consent
- If there is a request from an investigative agency according to the procedures and methods prescribed by the law for investigation purposes or as required by law
The Company, in principle, does not outsource the processing of users' personal information to external parties. However, exceptions are made in the following cases:
- If users have given prior consent
- If there is a request from an investigative agency according to the procedures and methods prescribed by the law for investigation purposes or as required by law
The information is promptly destroyed once feedback for customer inquiries related to company-related inquiries, service/product inquiries, and website inquiries is provided.
In principle, the Company promptly destroys personal information once the purpose of its collection and use has been achieved. The destruction procedures and methods are as follows:
1) Destruction Procedure: Information entered by the customer is stored for a certain period according to internal policies (see Retention and Usage Period) after the purpose is achieved, and then destroyed. The information is not used for any purpose other than retention, unless required by law.
2) Destruction Method: Personal information printed on paper is destroyed by shredding or incineration, and personal information stored in electronic file format is deleted using technical methods that prevent record recovery.
The Company takes the following technical, managerial, and physical measures to ensure security:
1) Establishment and Implementation of an Internal Management Plan: The Company establishes and implements an internal management plan to protect personal information.
2) Minimization and Training of Personal Information Processing Staff: Access rights to the database system processing personal information are granted, changed, or revoked to control access to personal information, and unauthorized access is controlled using an intrusion prevention system.
3) Storage and Prevention of Tampering of Access Records: Records of access to the personal information processing system (web logs, summary information, etc.) are stored and managed for at least six months, and security features are used to prevent tampering, theft, or loss of access records.
4) Technical Measures and Access Control Against Hacking: The Company installs security programs to prevent personal information leakage and damage due to hacking or computer viruses, regularly updates and checks them, and installs systems in areas with controlled access from outside. Technical and physical monitoring and blocking are implemented, including network traffic control (Monitoring) to detect illegal information changes and other attempts.
Users and legal representatives can view or correct the personal information of registered users at any time. Requests for access, correction, or deletion of personal information can be made to the Personal Information Manager by phone or email, and will be promptly processed after verification.
If a user requests correction of an error in their personal information, the information will not be used or provided until the correction is completed. If incorrect personal information has already been provided to a third party, the Company will promptly notify the third party of the correction to ensure the correction is made.
The Company processes and manages the termination or deletion of personal information requested by users or legal representatives according to the "Retention and Usage Period of Collected Personal Information" section, and ensures that it cannot be viewed or used for any other purpose.
Automatic personal information collection devices, such as cookies, are not operated when using internet services.
The Company designates the following departments and personnel in charge of personal information management to protect users' personal information and handle complaints related to personal information:
1) Department in Charge of Personal Information Management
Name:
Phone Number: - -
Email: @
2) Personal Information Manager
Name:
Phone Number: - -
Email: @
Users can report any complaints related to personal information protection while using the Company's services to the Personal Information Manager or the relevant department. The Company will promptly and sufficiently respond to users' reports. For further information or consultation regarding personal information infringement, please contact the following institutions:
1. Personal Information Dispute Mediation Committee (www.kopico.go.kr): 02-2100-2499
2. Supreme Prosecutors' Office Cyber Crime Investigation Team: 02-3480-3571 (http://www.spo.go.kr/)
3. National Police Agency Cyber Safety Bureau: 182 (No area code) (http://cyberbureau.police.go.kr/)
Persons who have suffered infringement of rights or interests due to the disposition or omission by the head of a public institution in accordance with the provisions of Articles 35 (Access to Personal Information), 36 (Correction or Deletion of Personal Information), and 37 (Suspension of Personal Information Processing, etc.) of the Personal Information Protection Act may request an administrative appeal in accordance with the procedures prescribed by the Administrative Appeals Act.
※ For detailed information on administrative appeals, please refer to the Ministry of Government Legislation (http://www.moleg.go.kr) website.
If there are any additions, deletions, or modifications to the current privacy policy, they will be notified through the 'Announcements' section on the website at least 7 days before the revision.
This website prohibits the unauthorized collection of email addresses posted on this site using email collection programs or other technical devices. Please be aware that violations of this policy will result in criminal penalties under the Information and Communications Network Act.